
Optimisation
Software Testing and QA Services
ELEKS’ custom-built quality assurance and testing services help you deliver a robust and UX-optimised product to market, up to 80% faster and 20% cheaper.
We Will Help You
Deliver a seamless UX
Our performance testing service helps you address issues with peak performance, responsiveness, security and stability, long before your end users ever see your product. So, you’ll be certain you’re delivering an experience worthy of your audience, with less risk of brand-damaging lag or downtime.
Reduce time-to-market
We’ll help you deliver your product to market up to 80% faster, with performance and test automation services that support continuous integration and deployment. Our tests are automated at every level, identifying problems early on so you can avoid reworks.
Cut development costs
ELEKS’ testing helps you identify issues early on in your SDLC, when they’re significantly less expensive to fix. You’ll also benefit from up to 20% lower testing costs, with our test automation service that reduces both human resource and testing time. And you can re-use your custom test scripts, at no extra expense.
Rapidly scale your business
We’ll help you implement continuous QA that allows you to quickly adapt to the changing needs of your customers, so you can focus on scaling your business. Our independent testing service offers you an impartial second opinion and a bigger likelihood of spotting pitfalls and risks.
Ensure software compliance
We’ll help you guarantee your software complies with the key quality standards: IEEE 829, ISO 29119, IEEE 730, ISO 25010, with a framework that adheres to industry standards across performance testing, independent testing and automated testing processes.
Verify the performance, usability and security of your product, quickly and cost-effectively.
Contact UsWhat’s Included
Software audit
Our software audit service will help you assess the quality of your code, along with the test coverage, security, user experience and integration layer so that you can make the necessary improvements to guarantee your product's integrity.
Performance testing
A testing service that helps you build responsive, stable and scalable applications, with an 80% shorter testing time frame.
Test automation
Reduces manual QA costs by up to 20%, by automating bug detection, eliminating human error and testing the resilience of your software.
Our Quality Assurance Success
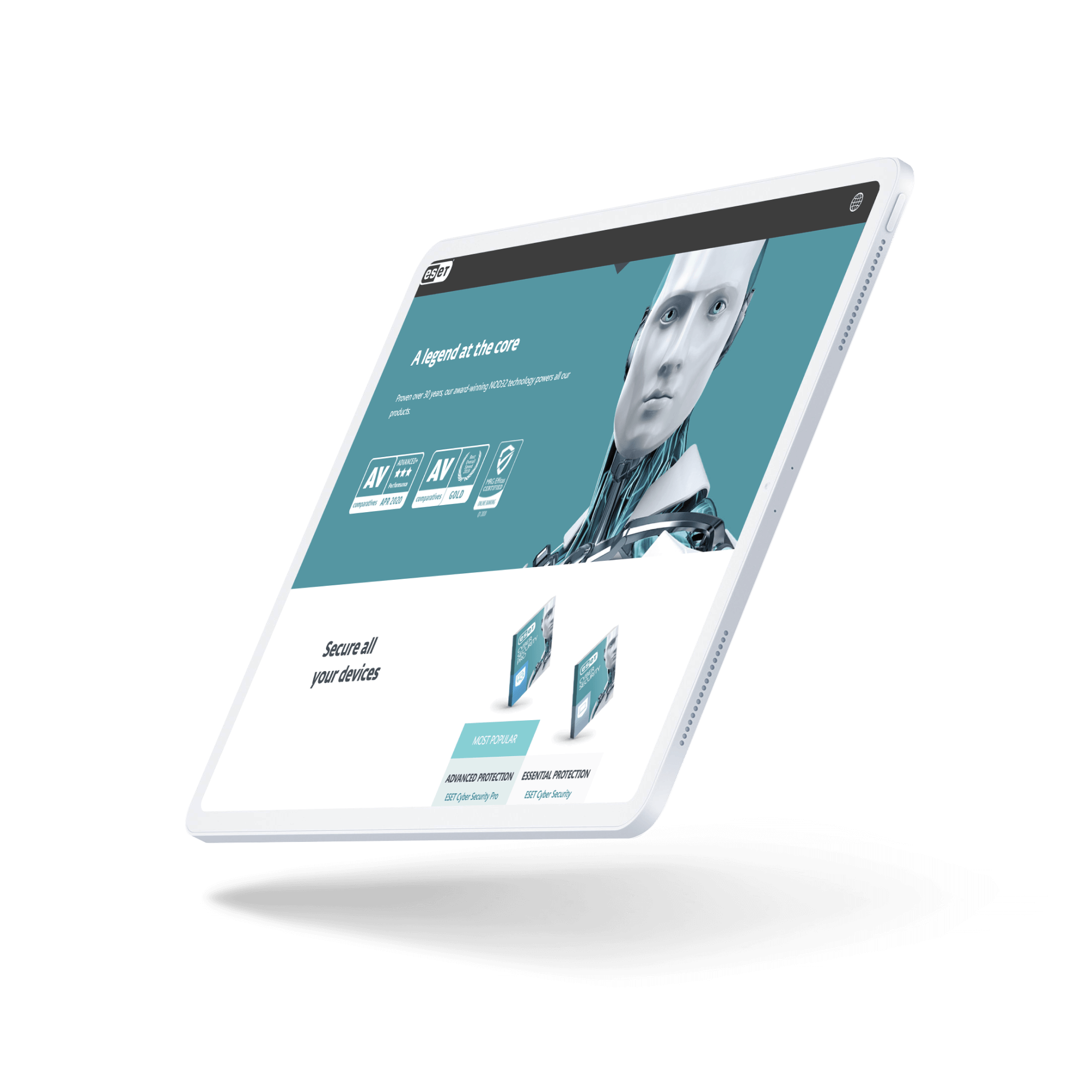
ESET Benefits from Hiring a Flexible QA Team and Assessing IT Security Risks
Faster product releases with a cost-efficient and flexible QA team
Stronger enterprise-wide security risk management
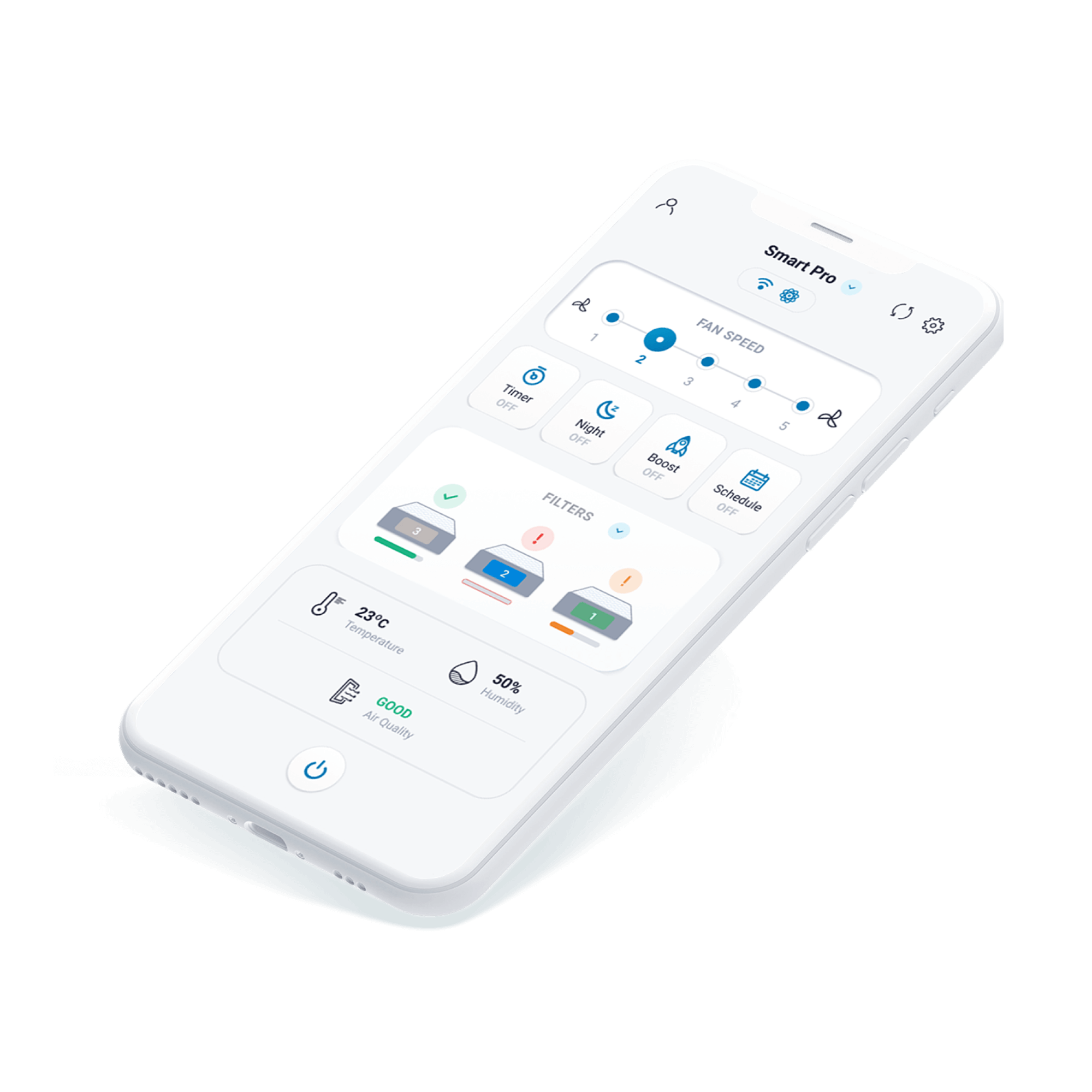
Seamless UХ for a Smart Air Disinfector’s Device Display and an IoT Remote Control App
Delivery of the solution in line with the defined budget and roadmap
Ensuring the app’s optimal usability and quality with a broad mix of design, QA and support services
Working with the team in ELEKS has given us a leading edge in bringing our new products to the market. Their team's technical knowledge, support and customer service is outstanding, and we consider them a key partner for all our software requirements.

Maranda Walsh
Director of Engineering
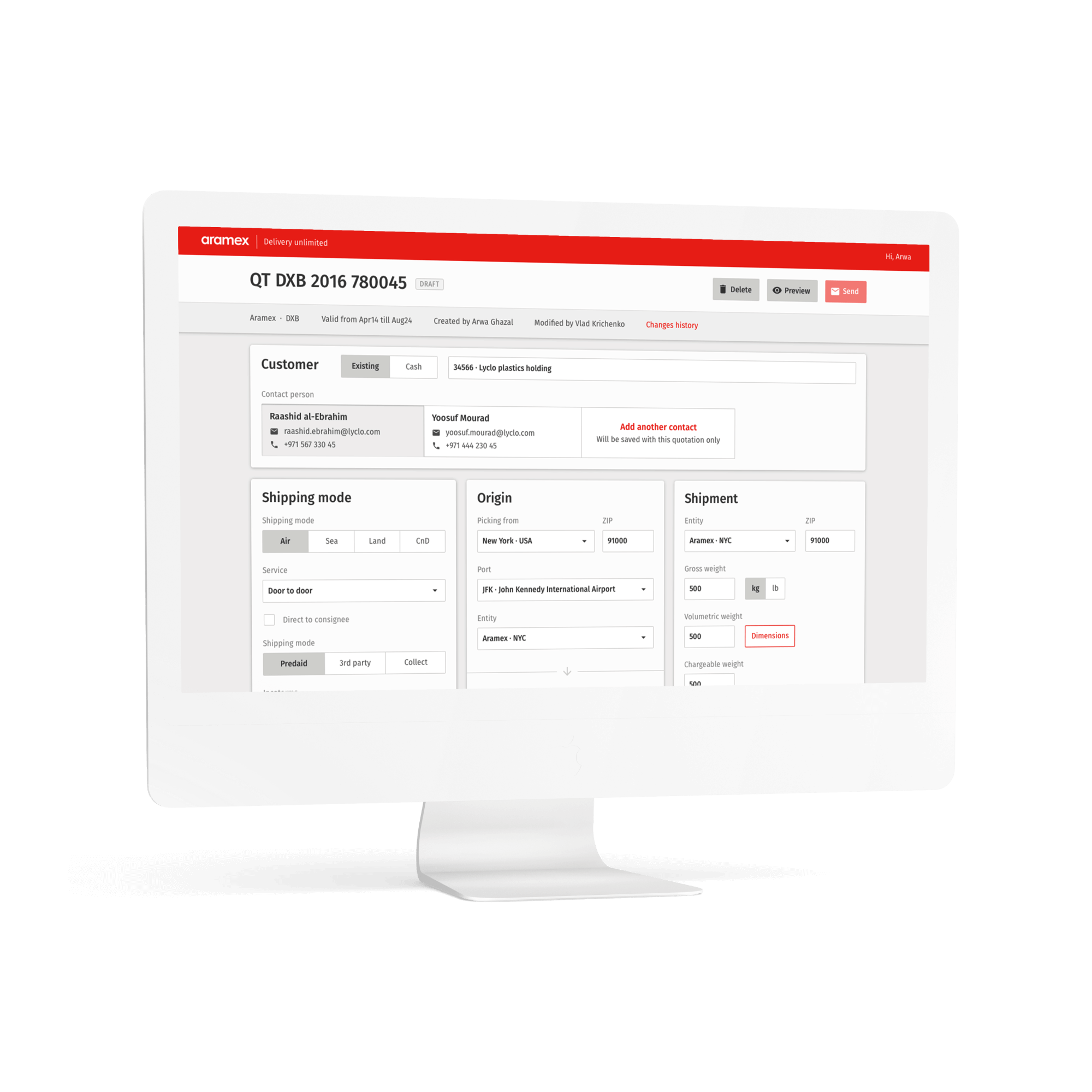
Building a Resilient Digital Ecosystem of a Logistics Enterprise
5x cost cut using apps for warehouse operations
230% increase in mobile user retention
ELEKS has been involved in the development of a number of our consumer-facing websites and mobile applications that allow our customers to easily track their shipments, get the information they need as well as stay in touch with us. We've appreciated the level of ELEKS' expertise, responsiveness and attention to details.

Samer Awajan
CTO, Aramex

Bringing a Complex Network Routing Solution to the Cloud
40% operational savings on product installation
20% reduction of support efforts
ELEKS impressed us with their depth of expertise and the ability to face complex technical problems. We were looking for a very specific skill set, and they provided us with just the right people. With ELEKS as our technology partner, we were able to not only revive our solution but also win over new markets and expand our customer base.

Gary Smith
Technical Director, Medusabusiness
Featured Content

Addressing The Limitations of Cypress Framework with Playwright and Selenium Injections

How to Improve E2E Testing for Web Apps with Playwright Automation
Playwright vs Cypress: Which Framework to Choose For E2E Testing?

Rendering Engines and Their Role in Automated Web Application Testing

Why Agile Doesn’t Work And 6 Ways You Can Fix This

Outsourcing Challenges Part 2: Offshore Software Development Team Structure

Mobile Test Automation with Appium: a Brief Framework Overview Addressing Common QA Pain Points

Penetration Testing vs Vulnerability Scanning: Which One Should I Use?

Does BDD Testing Live Up to its Hype?

Building Ranorex Framework with Visual Studio

