Fleets are increasingly connected – and open
Connected car features require code, indeed an explosion of in-vehicle code. Experts say a Ford pick-up truck contains applications with 130 million lines of code compared to a mere 6.5 million lines in a Boeing Dreamliner.
Furthermore, the benefits that transport and logistics software derive from connected vehicles depend on open communication – V2V (communications between vehicles) and V2X (communications between vehicles and other devices).
It is easy to imagine how a mix of open communications and large volumes of computer code creates the opportunity for malicious actors to pose threats to connected car security. In turn, logistics and transport operators need to be increasingly aware of cybersecurity threats where, in the past, cybersecurity was of little concerns.
Why connected car security poses a threat
Connected fleets present a disconcerting mix of physical dangers and privacy concerns. As we suggested, millions of lines of code alongside open connectivity present countless opportunities for hackers. The result is that malicious actors can take an opportunistic approach around several areas:
- Sniffing for data. Connected fleets will inevitably be transmitting a stream of data that can be intercepted and used for ill intent. This data can be sold on to the highest bidder, opening up the confidential internals of logistics operations, or simply creating further vulnerabilities through public exposure.
- Insider threats. Code and connectivity create opportunities for insiders that have plans and goals that run contrary to those of their employers. Stamping out the opportunities for actors that wish to manipulate data and connectivity for personal gain is extremely difficult, creating a trust issue - how can the data and operations of connected fleets be trusted in such an open environment?
- Manipulating vehicle sensors and features. While, in the past, cars were technology islands, the increasingly connected nature of cars implies that external actors can reach straight into vehicles to cause real-time damage, or to act out more subtly manipulative plans: manipulating fuel economy for example.
Clearly, logistics operators are at risk of losing a large degree of control with connected car security due to the code-intensive and open nature of today’s fleets.
Key connected car security touchpoints
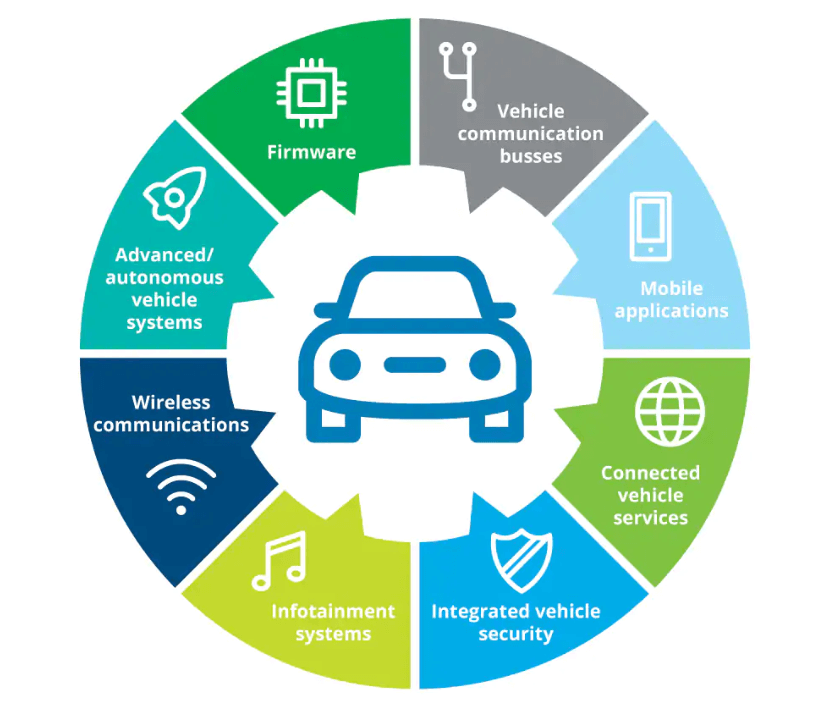
Image source: Deloitte analysis
Logistics operators can reduce the risks around connected car security by focusing on important security touchpoints.
- Infotainment. Of the millions of lines of code in vehicles, infotainment systems are responsible for a large chunk. Infotainment is rarely necessary for commercial use, companies can lock down these systems to minimise security risks.
- Connected services. V2V and V2X provide a wide attack surface and transport operators should thoroughly vet providers, and if possible, perform their own security analysis to probe security weaknesses.
- Autonomous vehicle systems. Self-driving vehicles are the future and companies that operate these vehicles need to confirm the integrity of these systems and do everything they can to limit security vulnerabilities.
- Firmware and communications busses. Core to the operations of intelligent cars, these building blocks can contain backdoors. Transport operators must make sure there are no hidden vulnerabilities in these systems and furthermore focus on enforcing tamper resistance.
These are just a few of the touchpoints in connected car security that companies must tie down. There is, however, a challenge in that the number of touchpoints is rapidly multiplying as vehicles become more intelligent, and more connected.
Taking a comprehensive approach to connected car security
With so many aspects of connected car security a cause for concern, logistics and transport operators need to take a very comprehensive approach to security. Doing so can be a challenge as transportation and logistics enterprises may short of the security expertise needed.
A recent study found software security is not keeping up with the technology of the automotive industry: 63% of respondents from the industry said they test less than half of their hardware, software and other technologies for vulnerabilities. Only 10% have an established cybersecurity team.
ELEKS has been delivering logistics software solutions for decades, helping companies optimise their operations. We are security experts too – trusted with the most business-critical of enterprise systems. As a result, we can deliver the security advice logistics operators need to minimise the growing risks from connected cars.
Get in touch to find how we can help your enterprise stay ahead of the threats modern transport fleets face.

Related Insights