
The COVID-19 pandemic has not only reinvented the way we live and work, but it has also resulted in a huge uptick in cybercrime. According to the Internet Crime Complaint Center, the number of cybercrimes reported has increased by 300% since the beginning of the pandemic.
At the start of the crisis, businesses rushed to go digital to survive and some neglected to implement appropriate security measures. Since then, work from home measures have also made it more difficult for companies to ensure the security of their systems. As a result, the number of cyberattacks has increased.
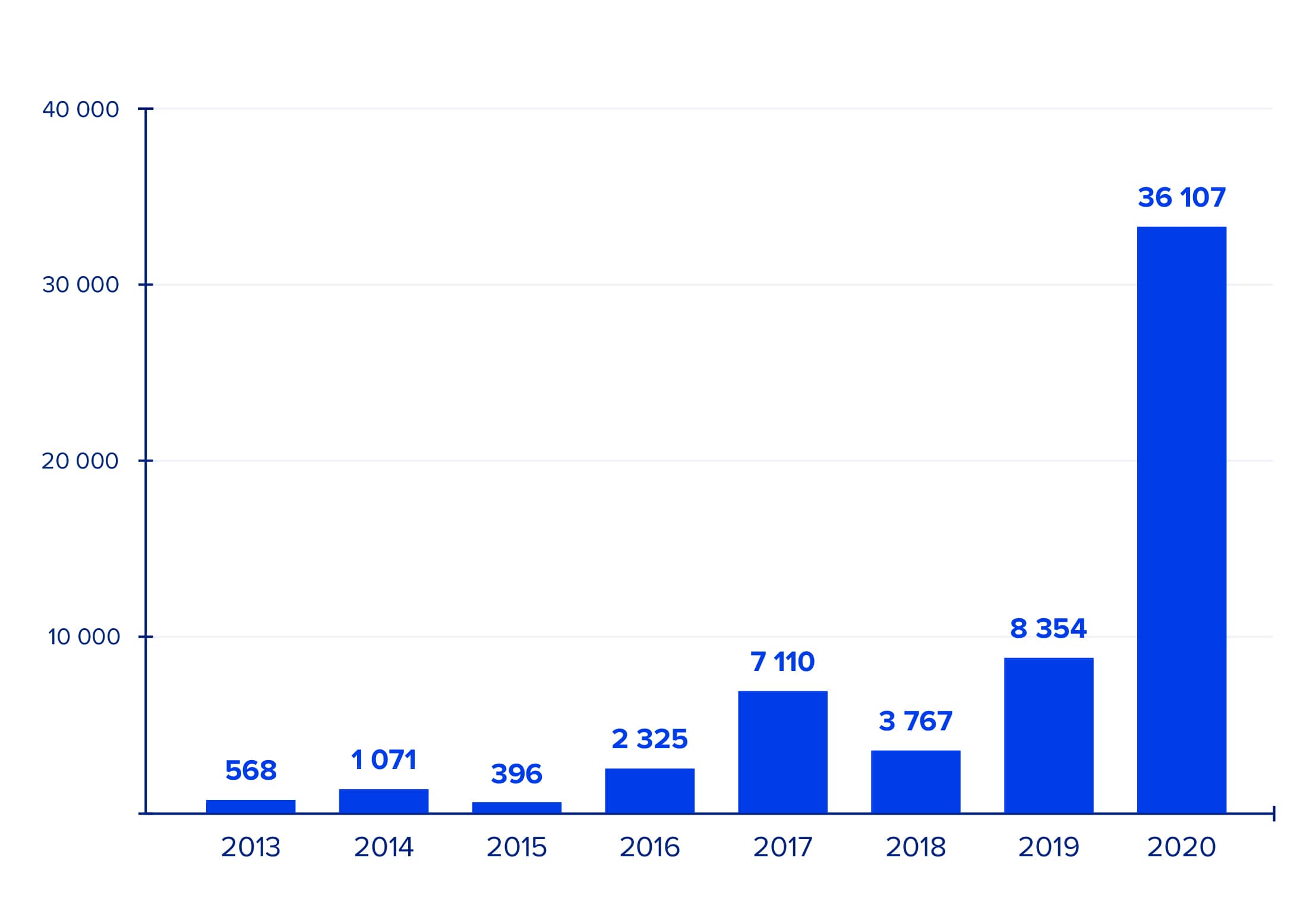
When investing in cloud computing services, businesses often overlook cybersecurity measures. As a result, cybercriminals are presented with opportunities and cybercrime statistics subsequently increase. The number of pandemic-related scams continues to rise. At first, cybercriminals were using COVID statistics for their scams. Google blocked 18 million COVID-related malware and phishing emails in just one week in April 2020. Now, the focus is shifting to unemployment and the Paycheck Protection Program (PPP).
By using both new tactics and more sophisticated attacks, cybercriminals are posing an enormous threat to safe business operations. In response, companies can partner with Security as a Service providers to ward off attacks and safeguard business processes.
What is Security as a Service?
Security as a Service – or SECaaS – is an outsourced service of business security management. It’s the provision of cloud-based security applications and services to clients’ cloud-based infrastructure or on-premises systems.
With the acceleration of global digitalisation, SECaaS ensures safe remote access to applications and services. Here's what can be included into the SECaaS offering:
- Identity and access management. Assuring the identity of a user or entity and granting the permitted level of access based on the verified identity.
- Data loss prevention. Monitoring, verifying and managing data security by implementing rules around actions that can be taken. For instance, such rules can deny the sending of documents that contain numbers that look like credit card numbers via email, or only allow specific users to access files from the fileserver, etc.
- Web security. Adding a protective layer to prevent malware from reaching the company through web browsing. This service can also create and enforce rules on types of web access for different users.
- Email security. Safeguarding businesses from phishing, malicious attachments and other threats by controlling inbound and outbound emails.
- Security assessments. Identifying the roots of risks by conducting an audit of cloud services and on-premises systems according to cybersecurity frameworks like NIST, ISO and CIS.
- Intrusion management. Detecting and reacting to unusual operations. The management process can involve real-time reconfiguration of system components to stop or avoid an intrusion.
- Security information and event management. Processing log and event information to immediately report and alert incidents or events which may require interference.
- Encryption. Encoding information with the help of cryptographic algorithms. Only the intended recipient can access the data by decoding it.
- Business continuity and disaster recovery. Introducing measures to guarantee the resilience of business operations in case of service interruptions caused by natural or human-made disasters or disruptions.
- Network security. Addressing network security controls by allocating access and then distributing, monitoring and protecting underlying resource services.
Learn more
What are the benefits of Security as a Service?
SECaaS provides resources to mitigate cyber threats from all sides. It can help to protect your network systems, cloud services, websites and many other services from the increasing number of cyberattacks, including malware, ransomware, phishing, viruses, denial of service (DoS), distributed denial of service (DDoS) and others.
Partnership with a SECaaS provider results in a plethora of immediate and long-term advantages, including:
- An experienced team. SECaaS providers give access to a pool of security specialists with high-level security expertise that is typically not available within an average organisation. Moreover, it is predicted that the number of unfilled cybersecurity jobs will reach 3.5 million in 2021. With a worrying market shortage of skilled cybersecurity specialists, SECaaS providers manage the need to hire and retain IT security staff.
- Latest security tools and services. SECaaS vendors consist of people who are aware of the latest developments in the cybersecurity field. For any security solutions and anti-viruses to be effective, they should be continuously updated. SECaaS specialists keep an eye on existing and emerging cyber threats and apply the latest security solutions to resist them.
- Cost reduction. The average cost of a data breach was $3.86 million in 2020. Once exposed to a cyberattack, a business may not only lose money as a result of paying a ransom but also as a result of covering the direct and indirect costs of the damage it causes, including regaining access to datasets and software. SECaaS providers work on preventing cyberattacks, keeping your business safe and protecting you from excessive threat-related expenditures. Moreover, you are likely to pay a fixed flat rate to your SECaaS vendor. Other costs related to in-house recruitment of skilled security experts, security infrastructure floorspace and purchasing multiple security solutions and keeping them updated will be covered by your SECaaS provider.
- Agility and scalability. Your security solution should adjust to your business’ growth and changes in operating processes or functions. The security solution should be scalable enough to add more users and devices if needed. On-premises security solutions are usually limited by the physical capacity of the infrastructure and the cost of expansion is high. SECaaS, on the other hand, is cloud-based, thus allows streamlined expansion when the need arises. With no physical restrictions, SECaaS is easily scalable with unlimited growth possibilities.
Should you consider Security as a Service?
In today’s rapidly evolving cybersecurity landscape, SECaaS offers a security model that brings great value to organisations and improves overall security. As a result, SECaaS saves money for businesses and reduces information security risks.
If you are looking for a reliable SECaaS provider who will, among other things, reduce your compliance burden, develop a robust security strategy and ensure the effectiveness of security controls, contact us today!

Related Insights








The breadth of knowledge and understanding that ELEKS has within its walls allows us to leverage that expertise to make superior deliverables for our customers. When you work with ELEKS, you are working with the top 1% of the aptitude and engineering excellence of the whole country.

Right from the start, we really liked ELEKS’ commitment and engagement. They came to us with their best people to try to understand our context, our business idea, and developed the first prototype with us. They were very professional and very customer oriented. I think, without ELEKS it probably would not have been possible to have such a successful product in such a short period of time.

ELEKS has been involved in the development of a number of our consumer-facing websites and mobile applications that allow our customers to easily track their shipments, get the information they need as well as stay in touch with us. We’ve appreciated the level of ELEKS’ expertise, responsiveness and attention to details.

