
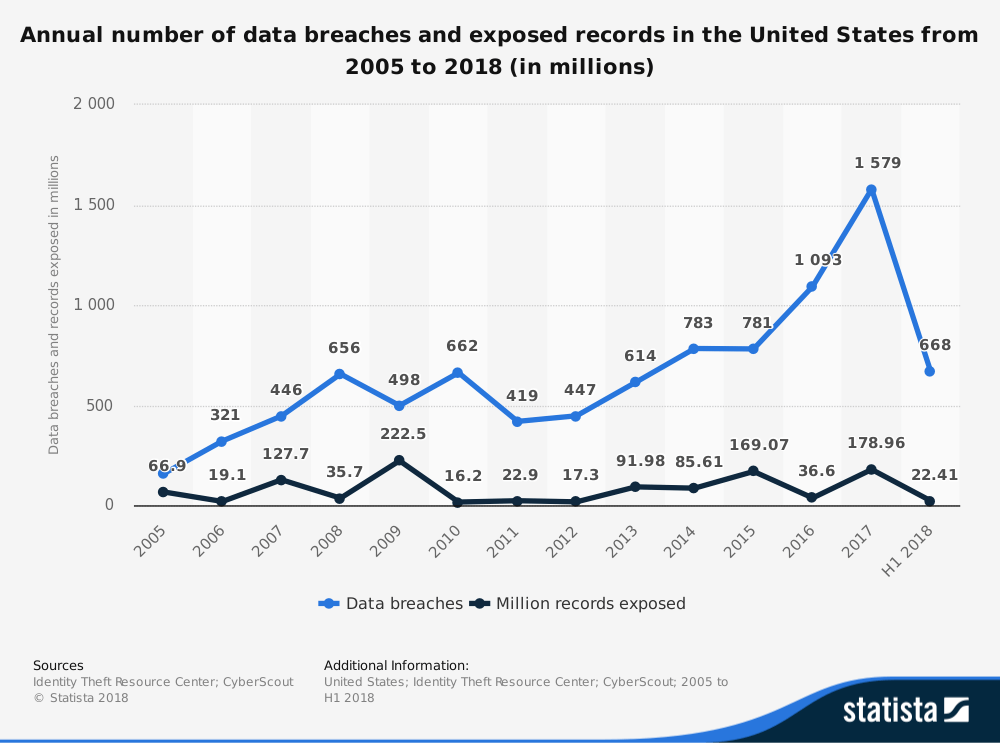
Statista says, between 2005 and the first half of 2018 the number of data breaches in the USA reached 668 with over 22 million records exposed.
According to Gartner, 35% of organisations currently use multiple data security tools, this is due to increase to 60% of organisations by 2020. One of these tools is data tokenization. While tokenization is often more secure than encryption, it is not always the answer. Let’s review the benefits and the week points of tokenization vs encryption to see which one is best for your organisation.
The difference between encryption and tokenization
Data encryption is a familiar tool that has seen decades of successful use, but the fact that it is reversible by design makes data encryption a vulnerable option. As a result, tokenization has emerged as one of the top technologies used by regulated industries to ensure information security – according to a PwC survey for the PCI.
However, to understand why data tokenization is a better solution under some scenarios we must first clarify the difference between encryption and tokenization.
Encryption
Data encryption is the process of using an algorithm combined with a unique code to translate data into a form that does not resemble the original and which carries no meaning in the absence of the unique code, or decryption key.
Encryption can be reversed and the data revealed if: the decryption key is stolen, or by brute-force attempts at discovering the encryption key. Herein lies the vulnerability of encrypted data: the actual data is still transmitted and can be illegally revealed by a determined actor.
Tokenization
Data tokenization takes a different approach. Any highly sensitive data such as credit card numbers is replaced with a token that uniquely identifies the data without containing the sensitive information.
A token has no intrinsic value or meaning, but it does allow for transactions to take place as the token maps to sensitive data, while the sensitive data itself remains securely stored, and not transmitted. However, tokenization can be resource-intensive and presents practical hurdles that data encryption does not.
It depends on your use case
Because tokenization avoids the transmission of sensitive data, it can be a more secure alternative to encryption, but tokenization is not suitable for unstructured data or large volumes of data.
When to consider encryption
Data encryption can efficiently apply a protective layer to large volumes of data without encumbering data transmission, or access by the recipient. In fact, for many general data protection use cases, data encryption offers the best mix of convenience, practicality, and security. Consider encryption for:
- Unstructured data, large volumes of data: Where your enterprise transmits large amounts of data such as images or video footage data encryption can provide effective protection without incurring large costs. Likewise, where data lacks the type of structure (ID numbers, credit card details, etc) that is required for token association encryption is a suitable alternative.
- Lower compliance requirements. Some data requires Fort Knox-like protection, and regulation such as PCI compliance and HIPAA demands matching protective measures. Other data sets require merely adequate protection, with an associated reduced motive for data theft. In these cases, encryption is the most cost-effective protective measure.
Where tokenization is the answer
Certain data sets such as credit card information pose such a risk of data theft that it is simply better to not transmit the actual data, instead tokenizing it. Tokenization can be a good fit under the following scenarios:
- Very strict compliance requirements. Where compliance requirements are truly onerous (think PCI DSS) it can simply be better not to handle the underlying data at all. Tokenization provides the opportunity to transact without handling data, limiting your exposure to compliance requirements.
- Structured data. Security gains and the associated efforts always involve a trade-off. However, where data has predictable structure tokenization becomes easier to apply. Consider tokenization if your data is highly structured.
- Where existing use is proven. While data encryption is standardised and easy to apply, data security using tokenization requires a more extensive rethink of systems and procedures. However, where tokenization has already proved to work your enterprise can adopt established practices to enjoy the same security advantages. Tokenization is already an extremely popular way to protect payment information, for example.
Choosing between encryption and tokenization
The choice between encryption and tokenization is not always straightforward. Besides, enterprises can be hesitant about adopting tokenization: just like blockchain, tokenization is a new concept that is not fully understood. For enterprises determined to discover the benefits of data tokenization taking the perceived risk could lead to huge security rewards.
Let’s discuss your security requirements and find an optimal approach to ensure your data is protected. Get in touch with us.
Related Insights







The breadth of knowledge and understanding that ELEKS has within its walls allows us to leverage that expertise to make superior deliverables for our customers. When you work with ELEKS, you are working with the top 1% of the aptitude and engineering excellence of the whole country.

Right from the start, we really liked ELEKS’ commitment and engagement. They came to us with their best people to try to understand our context, our business idea, and developed the first prototype with us. They were very professional and very customer oriented. I think, without ELEKS it probably would not have been possible to have such a successful product in such a short period of time.

ELEKS has been involved in the development of a number of our consumer-facing websites and mobile applications that allow our customers to easily track their shipments, get the information they need as well as stay in touch with us. We’ve appreciated the level of ELEKS’ expertise, responsiveness and attention to details.

